
Research projects focusing on intelligence and government solutions. Our research capabilities range from analysis and exploitation of known vulnerabilities to identifying new vulnerabilities in target software and developing custom proof-of-concept code.
Our research team is skilled in the following areas
- Operating systems
- Mobile devices
- Browsers
- Hypervisors
- Remote control systems
- Post-exploitation persistence
The research team represents the core of our services and is comprised of highly skilled researchers who are in close collaboration with the consulting and delivery teams.
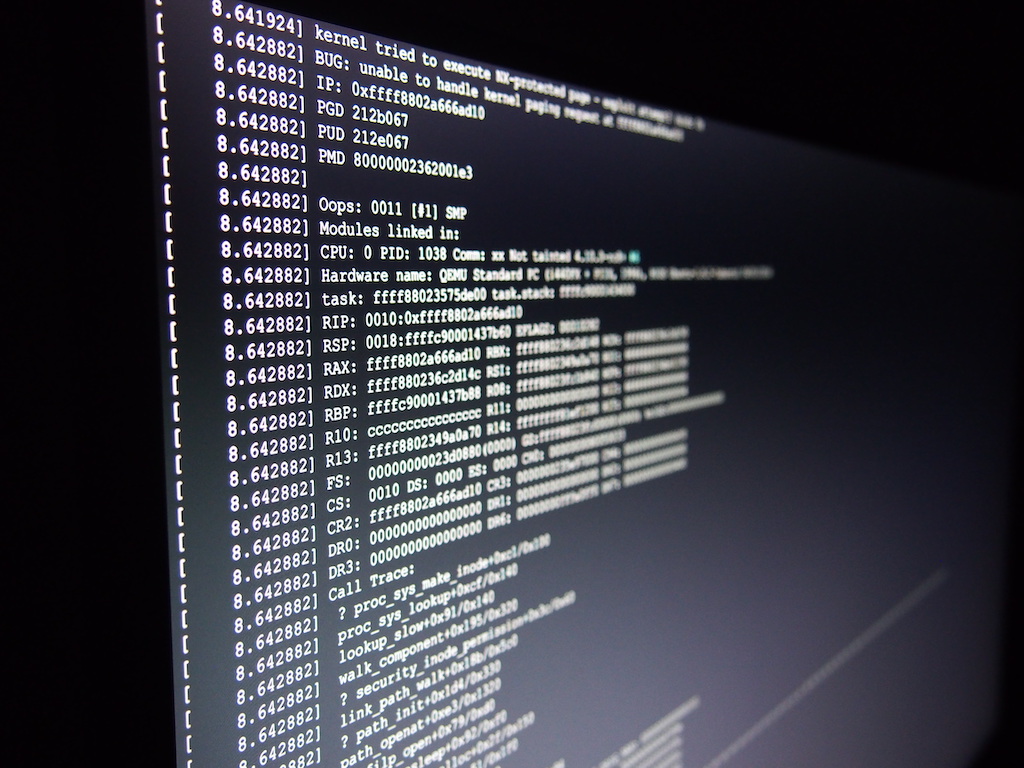
This course teaches common kernel exploitation techniques on modern Linux distributions (x86_x64 architecture and 3.x/4.x kernels). It provides up-to-date information on current kernel hardening implementations and exploit mitigations. It is designed for students already familiar with user-land exploitation who want to play with the heart of the OS and gain fundamental knowledge required to develop reliable and effective kernel exploits.
Even though this course is designed for beginners in kernel exploitation, a number of more advanced topics, such as reliable exploitation of heap vulnerabilities and SMEP/SMAP/KPTI bypasses, are discussed.
This course provides an overview of the Android kernel security describing the Android kernel attack surface and outlining any differences from the upstream Linux kernel. The main focus is on common kernel vulnerability classes and exploitation techniques on Android. The training is hands-on and assumes some familiarity with Linux kernel exploit development.
Kernel exploitation mitigations (Google and Samsung devices) are discussed and several bypass techniques will be presented. The course will also provide some introduction to fuzzing and crash analysis on Android devices.
ABN: 13634103405
